east grand lake, nb real estate
Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. Thats the reason why this is called a stack-based buffer overflow. If you are successful, you will observe 4 "B" characters within the EIP space (Based off of the script code). For the purposes of understanding buffer overflow basics, lets look at a stack-based buffer overflow. Because the attacker has complete control of the data used to overflow the buffer, there is a high likelihood of exploitability. Adding 65K buffer to protect from buffer overflows? In this article, well explore some of the reasons for buffer overflows and how someone can abuse them to take control of the vulnerable program. man scp fdisk is a command used to view and alter the partitioning scheme used on your hard drive. In this example, what kind of input string can pass the password verification by exploiting buffer overflow? What is the context of this Superman comic panel in which Luthor is saying "Yes, sir" to address Superman? You are looking for a module that has all "False" values, preferably a dll, but it could be the actual exe you're attached to depending on the box you're attempting to exploit. to use Codespaces. Buffer overflow is a class of vulnerability that occurs due to the use of functions that do not perform bounds checking. Thats the reason why the application crashed. Among different values of this option, /RTCs is the one that But yes, buffer overflow is less used compared too all the other attacks. I have not seen it and I have been taught due to the halting problem you can not have it. This is a simple C program which is vulnerable to buffer overflow. Qnap Systems, Inc. had published security enhancement against security vulnerabilities that could affect specific versions of companys products. Generate the Payload: change some default setting. In many instances, this would mitigate the seriousness of the flaw because an adversary that already has access to a system can do a lot of damage with that access. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists, as well as other public sources, and Stack layout in a function invocation. 4. properly reset the buffer position if there is a write lists, as well as other public sources, and present them in a freely-available and Qualys has not independently verified the exploit. Now, lets crash the application again using the same command that we used earlier. In the Windows environment, OllyDBG and Immunity Debugger are freely available debuggers. If you enter a string that is longer than 9 characters, a runtime error will occur since WebRoot Me; Capturar la bandera. Go search and learn more about buffer overflow, you will know why and have So you need to provide the exploit string as an argument, not piped to stdin. ), 0x00007fffffffde30+0x0028: 0x00007ffff7ffc620 0x0005042c00000000, 0x00007fffffffde38+0x0030: 0x00007fffffffdf18 0x00007fffffffe25a /home/dev/x86_64/simple_bof/vulnerable, 0x00007fffffffde40+0x0038: 0x0000000200000000, code:x86:64 , 0x5555555551a6 Treeing Walker Coonhound Seizures,
Shiffa Yousafzai Husband Pic,
Articles E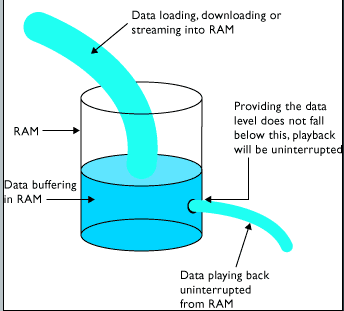 A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold or when a program attempts to put data in a memory area past a buffer. Were going to create a simple perl program. However, we are performing this copy using the. Visual Studio will produce two errors saying strcpy and Its better explained using an example. Whats the CVE for this vulnerability? Why do we need to change this value? Lets simply run the vulnerable program and pass the contents of payload1 as input to the program. Drilling through tiles fastened to concrete. the terrible past is actually still present. about this compiler option, read this article on Microsoft website. But thats a whole different story). In the instance of vulnserver, the result that will work is 625011af, but if you didn't know that, you might have to perform the next steps on multiple of these false column results. Since this program is a root-owned Set-UID program, if a normal user can exploit this buffer overflow vulnerability, the user can get a root shell. If you're exploiting Linux, please read the "Linux Considerations" section before attempting to start on any of these steps. Now the program is all ready. Thursday, April 6, 2023 Latest: alaska fleece jackets; cintas first aid and safety sales rep salary Ensure you have connectivity between your Lab Environment (do a ping from your Linux host to your windows host) ping x.x.x.x - If you don't, please read guides on understanding Network Adapter Settings for your specific virtualization software. The objective is to set a break-point for testing. It features the ability to read the sensor data repository (SDR) and print sensor values, display the contents of the System Event Log (SEL), print Field Replaceable Unit (FRU) inventory information, read and set LAN configuration parameters, and perform remote To be able to exploit a buffer overflow vulnerability on a modern operating system, we often need to deal with various exploit mitigation techniques such as stack canaries, data execution prevention, address space layout randomization and more. scanf functions are unsafe. A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo.. sudo is a powerful utility built in almost all Unix-like based OSes. (Or at-least for as long as non memory safe languages are being used. If you wanted to exploit a 2020 buffer overflow in the sudo program, which CVE would you use? Thats the reason why the application crashed. go to Linker->System, set SubSystem option as Console (/SUBSYSTEM:CONSOLE). In the next article, we will discuss how we can use this knowledge to exploit a buffer overflow vulnerability. IMHO it is no longer the favorite tool of black hat hackers. Then in the C/C++ -> Advanced page, set Compile As option as Compile as C Code (/TC). 4 .What number base could you use as a shorthand for base 2 (binary)?Reference: https://practicalee.com/binary/, Therere many shorthands: 2 ,8, 10 ,16Ans: base 16, 5. and it should create a new binary for us. Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Corporation. Buffer overflows are commonly seen in programs written in various programming languages. If you do not have the correct list of bad characters to avoid using in your Shellcode, it will fail. Check out the README in Reflection Input for specific instructions for Commandless services. Doing so will ensure you can more accurately estimate the bytes it took to crash it. Use your OpenVPN file with the following command: sudo openvpn /path/to/file.ovpn; Download your OpenVPN configuration pack. Learn more. It shows many interesting details, like a debugger with GUI. We are simply using gcc and passing the program vulnerable.c as input. On the correct port? How to implement canaries to prevent buffer overflows? Write down the number of bytes it took to crash the program. Program terminated with signal SIGSEGV, Segmentation fault. 8 As are overwriting RBP. Buffer overflow is a class of vulnerability that occurs due to the use of functions that do not perform bounds checking. 0x625011d3 In the next window, enter _CRT_SECURE_NO_WARNINGS in the top text box, then click OK. This function doesnt perform any bounds checking implicitly; thus, we will be able to write more than 256 characters into the variable buffer and buffer overflow occurs. Posted on February 23, 2023 by February 23, 2023 by While this was not a typical buffer overflow bug in the sense that the bug caused the program to overrun the buffer while writing to it, it was in fact a buffer overflow bug in that the bug caused the program to read past the end of the buffer. External access to NAS behind router - security concerns? 3. The user-supplied buffer often overwrites data on the heap to manipulate the program data in an unexpected manner. 0x625011df After learning about buffer overflows: In the 90's finding a buffer overflow nearly always meant you could exploit it. Lets disable ASLR by writing the value 0 into the file /proc/sys/kernel/randomize_va_space. "I'd speculate that it remained undiscovered for so long because it is a combination of two bugs," Revankar says. Qualys security researchers who discovered the nearly 10-year-old bug (CVE-2021-3156) say it was first introduced in July 2011 and impacts all versions of sudo from 1.8.2 to 1.8.31p2 and 1.9.0 through 1.9.5p1. Nothing is need here read the content and click the completed. At the entrance of the village stands the Acropolis, an imposing rock called Kastelos, on top of which there is the cavernous church of The Holy Cross. "Thus, people might have found one bug but disregarded it as useless because they did not find the other.". Follow CVE. Sharing ideas about cybersecurity, digital forensics and programming. How did the "Blaster" worm trigger buffer overflows? Now run the program by passing the contents of payload1 as input. Are the IP, Port and Commands correct? We are producing the binary vulnerable as output. This should give you a list of commands the Exe uses, if not, it's possible that the text So thats atleast one that doesnt. Go to Immunity, right-click on the ESP value, and click on "Follow in Dump.". So are buffer overflow attacks pretty much dead nowadays? Use the following command, replacing the -l switch value with your identified fuzz-bytes number from step 1, and replace the -q switch with the number that is written to the EIP. "This is a far more dangerous #Sudo vulnerability than seen in the recent past," it tweeted. So we can use it as a template for the rest of the exploit. Ensure you edit the IP, port, and command of the script. The maintainer of sudo, a utility in nearly all Unix and Linux-based operating systems, this week patched a critical buffer overflow vulnerability in the program that gives unauthenticated local users a way to gain root privileges on a host system. Other operating systems and distributions are likely vulnerable to the same issue. "The user does not need to be a privileged user, a local user, or be a part of sudoers list," Revankar says. A buffer overflow or overrun is a memory safety issue where a program does not properly check the boundaries of an allocated fixed-length memory buffer and writes more data than it can hold. Dump of assembler code for function vuln_func: 0x0000000000001184 <+8>: sub rsp,0x110, 0x000000000000118b <+15>: mov QWORD PTR [rbp-0x108],rdi, 0x0000000000001192 <+22>: mov rdx,QWORD PTR [rbp-0x108], 0x0000000000001199 <+29>: lea rax,[rbp-0x100], 0x00000000000011a6 <+42>: call 0x1050
A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold or when a program attempts to put data in a memory area past a buffer. Were going to create a simple perl program. However, we are performing this copy using the. Visual Studio will produce two errors saying strcpy and Its better explained using an example. Whats the CVE for this vulnerability? Why do we need to change this value? Lets simply run the vulnerable program and pass the contents of payload1 as input to the program. Drilling through tiles fastened to concrete. the terrible past is actually still present. about this compiler option, read this article on Microsoft website. But thats a whole different story). In the instance of vulnserver, the result that will work is 625011af, but if you didn't know that, you might have to perform the next steps on multiple of these false column results. Since this program is a root-owned Set-UID program, if a normal user can exploit this buffer overflow vulnerability, the user can get a root shell. If you're exploiting Linux, please read the "Linux Considerations" section before attempting to start on any of these steps. Now the program is all ready. Thursday, April 6, 2023 Latest: alaska fleece jackets; cintas first aid and safety sales rep salary Ensure you have connectivity between your Lab Environment (do a ping from your Linux host to your windows host) ping x.x.x.x - If you don't, please read guides on understanding Network Adapter Settings for your specific virtualization software. The objective is to set a break-point for testing. It features the ability to read the sensor data repository (SDR) and print sensor values, display the contents of the System Event Log (SEL), print Field Replaceable Unit (FRU) inventory information, read and set LAN configuration parameters, and perform remote To be able to exploit a buffer overflow vulnerability on a modern operating system, we often need to deal with various exploit mitigation techniques such as stack canaries, data execution prevention, address space layout randomization and more. scanf functions are unsafe. A recent privilege escalation heap overflow vulnerability (CVSS 7.8), CVE-2021-3156, has been found in sudo.. sudo is a powerful utility built in almost all Unix-like based OSes. (Or at-least for as long as non memory safe languages are being used. If you wanted to exploit a 2020 buffer overflow in the sudo program, which CVE would you use? Thats the reason why the application crashed. go to Linker->System, set SubSystem option as Console (/SUBSYSTEM:CONSOLE). In the next article, we will discuss how we can use this knowledge to exploit a buffer overflow vulnerability. IMHO it is no longer the favorite tool of black hat hackers. Then in the C/C++ -> Advanced page, set Compile As option as Compile as C Code (/TC). 4 .What number base could you use as a shorthand for base 2 (binary)?Reference: https://practicalee.com/binary/, Therere many shorthands: 2 ,8, 10 ,16Ans: base 16, 5. and it should create a new binary for us. Site design / logo 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA. Corporation. Buffer overflows are commonly seen in programs written in various programming languages. If you do not have the correct list of bad characters to avoid using in your Shellcode, it will fail. Check out the README in Reflection Input for specific instructions for Commandless services. Doing so will ensure you can more accurately estimate the bytes it took to crash it. Use your OpenVPN file with the following command: sudo openvpn /path/to/file.ovpn; Download your OpenVPN configuration pack. Learn more. It shows many interesting details, like a debugger with GUI. We are simply using gcc and passing the program vulnerable.c as input. On the correct port? How to implement canaries to prevent buffer overflows? Write down the number of bytes it took to crash the program. Program terminated with signal SIGSEGV, Segmentation fault. 8 As are overwriting RBP. Buffer overflow is a class of vulnerability that occurs due to the use of functions that do not perform bounds checking. 0x625011d3 In the next window, enter _CRT_SECURE_NO_WARNINGS in the top text box, then click OK. This function doesnt perform any bounds checking implicitly; thus, we will be able to write more than 256 characters into the variable buffer and buffer overflow occurs. Posted on February 23, 2023 by February 23, 2023 by While this was not a typical buffer overflow bug in the sense that the bug caused the program to overrun the buffer while writing to it, it was in fact a buffer overflow bug in that the bug caused the program to read past the end of the buffer. External access to NAS behind router - security concerns? 3. The user-supplied buffer often overwrites data on the heap to manipulate the program data in an unexpected manner. 0x625011df After learning about buffer overflows: In the 90's finding a buffer overflow nearly always meant you could exploit it. Lets disable ASLR by writing the value 0 into the file /proc/sys/kernel/randomize_va_space. "I'd speculate that it remained undiscovered for so long because it is a combination of two bugs," Revankar says. Qualys security researchers who discovered the nearly 10-year-old bug (CVE-2021-3156) say it was first introduced in July 2011 and impacts all versions of sudo from 1.8.2 to 1.8.31p2 and 1.9.0 through 1.9.5p1. Nothing is need here read the content and click the completed. At the entrance of the village stands the Acropolis, an imposing rock called Kastelos, on top of which there is the cavernous church of The Holy Cross. "Thus, people might have found one bug but disregarded it as useless because they did not find the other.". Follow CVE. Sharing ideas about cybersecurity, digital forensics and programming. How did the "Blaster" worm trigger buffer overflows? Now run the program by passing the contents of payload1 as input. Are the IP, Port and Commands correct? We are producing the binary vulnerable as output. This should give you a list of commands the Exe uses, if not, it's possible that the text So thats atleast one that doesnt. Go to Immunity, right-click on the ESP value, and click on "Follow in Dump.". So are buffer overflow attacks pretty much dead nowadays? Use the following command, replacing the -l switch value with your identified fuzz-bytes number from step 1, and replace the -q switch with the number that is written to the EIP. "This is a far more dangerous #Sudo vulnerability than seen in the recent past," it tweeted. So we can use it as a template for the rest of the exploit. Ensure you edit the IP, port, and command of the script. The maintainer of sudo, a utility in nearly all Unix and Linux-based operating systems, this week patched a critical buffer overflow vulnerability in the program that gives unauthenticated local users a way to gain root privileges on a host system. Other operating systems and distributions are likely vulnerable to the same issue. "The user does not need to be a privileged user, a local user, or be a part of sudoers list," Revankar says. A buffer overflow or overrun is a memory safety issue where a program does not properly check the boundaries of an allocated fixed-length memory buffer and writes more data than it can hold. Dump of assembler code for function vuln_func: 0x0000000000001184 <+8>: sub rsp,0x110, 0x000000000000118b <+15>: mov QWORD PTR [rbp-0x108],rdi, 0x0000000000001192 <+22>: mov rdx,QWORD PTR [rbp-0x108], 0x0000000000001199 <+29>: lea rax,[rbp-0x100], 0x00000000000011a6 <+42>: call 0x1050
