tacacs+ advantages and disadvantages
The sequential methods used in Authentication will be via: In addition, all terminal lines will be configured so that they are authenticated using AAA. This option tells the AAA engine not to attempt any other Authentication methods, meaning that the Authentication process ceases at this point. Please note that other Pearson websites and online products and services have their own separate privacy policies. Information is taken from the packet header and the pre-shared key calculates a series of hashes. The AAA framework uses a set of three independent function which are: Authentication is based on verifying user credentials, which can be any of the following: Something the user knows which is referred to as Authentication by knowledge, Something the user possesses which is referred to as Authentication by possession. AAA server groups are configured by using the aaa group server [radius|tacacs+][name] global configuration command. Although both methods are valid, it is important to keep in mind that the local user database supports only a limited number of Cisco-specific security attribute-values, but server-based AAA provides more capabilities and security information is stored on the server, not the network device. Kerberos is a trusted third-party Authentication Layer 7 (Application Layer) service. heriberto lopez height This keyword configures Accounting for network-related services, such as PPP. Question: How does TACACS+ work? Each hash has the previous hash linked into its input values, and the end result is referred to as the pseudo pad. Before we get into the specifics of RADIUS and TACACS+, let's define the different parts of AAA solutions. This option also allows the administrator to specify the AAA ports that the RADIUS server will use. In later development, vendors extended TACACS. If a single administrator wants to access 100 routers and the local database of the device is used for username and password (authentication) then the administrator has to make the same user account at different times. The owner has full-fledged control over the rules and can The Access-Request packet will also contain other information on the type of session that the user wants to initiate. TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. TACACS+ provides detailed accounting information and flexible administrative control over authentication and authorization processes. Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. It provides greater granular control (than RADIUS) as the commands that are authorized to be used by the user can be specified. This keyword is used to specify the duration that the NAS will wait for the TACACS+ server to respond before moving on to the next method specified. This is illustrated in step 3. Accounting records are also made up of accounting AV pairs. This keyword is used to specify RADIUS IP parameters. Accounting methods must be defined through AAA. It is important to remember that, depending on the Cisco IOS version your NAS is running, these commands can be performed on a single line or they may need to be implemented on a line-by-line basis. The client is then responsible for enforcing user access control based on those AV pairs. username-prompt Text to use when prompting for a username. Keep in mind that only the packet payload is encrypted; the packet header is always sent in clear text. banner Message to use when starting login/authentication. The request is accepted and the configure terminal command is successfully authorized on R1, as illustrated in step 4. The sequential methods to be used will be the local user database. (telnet, rlogin). TACACS+ which stands for Terminal Access Controller Access Control Server is a security protocol used in the AAA framework to provide centralized Authorization provides the capability to enforce policies for network resources after the user has been successfully authenticated. RADIUS stands for Remote Authentication Dial-In User Service. Method lists allow control of one or more security protocols and security servers to be used to offer fault tolerance and backup of Authentication databases. Either method is acceptable and produces the same end result. The server can respond with one of the following reply messages: For accounting, the client will send a REQUEST message to the TACACS+ server for which the server responds with a RESPONSE message stating that the record is received. Also, authorization (means what the user is authorized to do) can be configured. By default, the Cisco IOS will use UDP port 1646, which is the port defined in RFC 2138. A network device can log every user who authenticates a device as well as every command the user runs (or attempts to run).  TACACS is really nice to have. The keywords that fall within the scope of the IINS course requirements are described in the following table: The following example illustrates how to configure a TACACS+ server group named IINS-TACACS. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. Pearson will not use personal information collected or processed as a K-12 school service provider for the purpose of directed or targeted advertising. The following diagram illustrates the sequence of messages that are exchanged: Following the diagram illustrated above, in step 1, the remote user dials in to the NAS. As it is Cisco proprietary, therefore it can be used between the Cisco devices only. Login to this site requires ssl communication. In larger organizations, however, tracking who has access to what devices at what level can quickly become complex. We communicate with users on a regular basis to provide requested services and in regard to issues relating to their account we reply via email or phone in accordance with the users' wishes when a user submits their information through our Contact Us form. commands For exec (shell) commands. This message indicates that request is authorized and the information returned in the RESPONSE packet is used in addition to the requested information. Webtacacs+ advantages and disadvantages. What are its disadvantages?
TACACS is really nice to have. The keywords that fall within the scope of the IINS course requirements are described in the following table: The following example illustrates how to configure a TACACS+ server group named IINS-TACACS. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. Pearson will not use personal information collected or processed as a K-12 school service provider for the purpose of directed or targeted advertising. The following diagram illustrates the sequence of messages that are exchanged: Following the diagram illustrated above, in step 1, the remote user dials in to the NAS. As it is Cisco proprietary, therefore it can be used between the Cisco devices only. Login to this site requires ssl communication. In larger organizations, however, tracking who has access to what devices at what level can quickly become complex. We communicate with users on a regular basis to provide requested services and in regard to issues relating to their account we reply via email or phone in accordance with the users' wishes when a user submits their information through our Contact Us form. commands For exec (shell) commands. This message indicates that request is authorized and the information returned in the RESPONSE packet is used in addition to the requested information. Webtacacs+ advantages and disadvantages. What are its disadvantages?  who the user is. Save up to 70% on N10-008 exam prep and validate your skills. TACACS+ RESPONSE messages are sent by the server and contain one of the following: PASS_ADD (indicates that request is authorized), PASS_REPL ( sent by the AAA server when it ignores the request), FOLLOW ( the AAA wants to have Authorization performed on another server), ERROR (indicates indicate an error on the AAA server), TACACS+ Accounting also uses REQUEST and the RESPONSE messages, TACACS+ Accounting takes place by sending a record to the AAA server. Some of the more common AV pairs used by TACACS+ are provided later in this chapter. The options available for Authorization in the Cisco IOS software are as follows: auth-proxy For Authentication Proxy Services, cache For AAA cache configuration. This keyword is used to specify the password prompt that users will see when authenticating. RADIUS was created by Livingston Enterprises but is now defined in RFC 2138 and RFC 2139. This information may be stored locally, i.e. Before we progress any further, we are going to look at the options provided by this command and what they are used for; however, because some of the options are beyond the scope of the IINS course requirements, we will be looking at only those that are applicable at this level. As the user session progresses, the NAS periodically sends interim update records. To make this discussion a little clearer, we'll use an access door system as an example. This 1-byte field defines whether the packet is used for Authentication, Authorization, or Accounting. Having stated that, we will now move on to the second part of the AAA framework: Authorization.
who the user is. Save up to 70% on N10-008 exam prep and validate your skills. TACACS+ RESPONSE messages are sent by the server and contain one of the following: PASS_ADD (indicates that request is authorized), PASS_REPL ( sent by the AAA server when it ignores the request), FOLLOW ( the AAA wants to have Authorization performed on another server), ERROR (indicates indicate an error on the AAA server), TACACS+ Accounting also uses REQUEST and the RESPONSE messages, TACACS+ Accounting takes place by sending a record to the AAA server. Some of the more common AV pairs used by TACACS+ are provided later in this chapter. The options available for Authorization in the Cisco IOS software are as follows: auth-proxy For Authentication Proxy Services, cache For AAA cache configuration. This keyword is used to specify the password prompt that users will see when authenticating. RADIUS was created by Livingston Enterprises but is now defined in RFC 2138 and RFC 2139. This information may be stored locally, i.e. Before we progress any further, we are going to look at the options provided by this command and what they are used for; however, because some of the options are beyond the scope of the IINS course requirements, we will be looking at only those that are applicable at this level. As the user session progresses, the NAS periodically sends interim update records. To make this discussion a little clearer, we'll use an access door system as an example. This 1-byte field defines whether the packet is used for Authentication, Authorization, or Accounting. Having stated that, we will now move on to the second part of the AAA framework: Authorization. 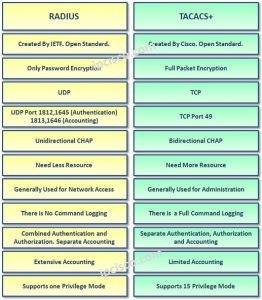 enable Set authentication list for enable. The STOP record indicates when a service is about to stop or when a service is stopped. In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. This method list is also applied to all terminal lines on the router (this example assumes that Authentication has been configured and, thus, focuses only on Authorization commands), as follows: R2(config-line)#authorization commands 15 COMND-AUTHOR. The first example illustrates how to configure Authorization for PPP (network) using the method list PPP-AUTHOR. The TACACS+ packet header is illustrated in the following diagram: This 4-bit field indicates the major TACACS+ version number. The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6.
enable Set authentication list for enable. The STOP record indicates when a service is about to stop or when a service is stopped. In addition to the standard set of attributes, RADIUS also specifies the vendor-specific attribute (Attribute 26) that allows vendors to support their own extended attributes, which may be specifically tailored to their particular application and are not for general use. This method list is also applied to all terminal lines on the router (this example assumes that Authentication has been configured and, thus, focuses only on Authorization commands), as follows: R2(config-line)#authorization commands 15 COMND-AUTHOR. The first example illustrates how to configure Authorization for PPP (network) using the method list PPP-AUTHOR. The TACACS+ packet header is illustrated in the following diagram: This 4-bit field indicates the major TACACS+ version number. The name is found and the TACACS+ server sends a request for a password (REPLY), as illustrated in step 6.  These methods are applied to specific interfaces or even terminal lines (e.g. Clients query the AAA server to determine what actions a user is authorized to perform, and the server provides AV pairs that define user authorization. This is where authentication, authorization, and accounting (AAA) solutions come to the rescue. To address this issue, a new open-standard security protocol, called DIAMETER, has been proposed to replace RADIUS. This keyword configures Accounting for all system-level events. AAA provides a flexible, modular solution for controlling access to the network. With a TACACS+ server, it's possible to implement command control using either access levels (which are further configured on the devices) or using command-by-command authorization based on server users and groups. password-prompt Text to use when prompting for a password. AAA allows devices to point to multiple security servers, often referred to as server groups. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the If this limit is reached, the current session between the client and the TACACS+ server is reset and a new session is established. WebAdvantages/Strengths of VPN-. tacacs+ advantages and disadvantages. the services available to the user. This is an authorization level label for Kerberos principals. Credentials are used to verify the identity of a user or service. The third, and final, example demonstrates how to configure Authentication for all logins using a method list named LOGIN-LIST. Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. Accounting provides the means to capture resource utilization by collecting and sending information that can be used for billing, auditing, and reporting to the security server. The Authorization process is performed using a session that consists of this pair of messages. This can be an external server that operates well. The following table describes the keywords that you are expected to be familiar with when configuring Authorization: Once you have selected the service you want to authorize, you must then select the method list to use for Authorization. Cisco ASA and PIX) configuration is beyond the scope of the IINS course requirements, you are required to know how to implement AAA services on Cisco IOS devices. It is important to understand that the encryption of the TACACS+ packet is not the same as that of traditional user data. This is not a desirable trait (due to reasons beyond the scope of the IINS course requirements); therefore, we will not be discussing this keyword in any further detail. Provides greater granular control than RADIUS.TACACS+ allows a network administrator to define what commands a user may run. This keyword is used to configure a banner for login Authentication. Modern RADIUS uses User Datagram Protocol (UDP) ports 1812 (authentication) and 1813 (accounting) for communications, while some older implementations may use ports 1645 (authentication) and 1646 (accounting). Authorization is the next step in this process. arrow_forward. VPN bypasses network congestion from untrusted sources. Transcribed image text: This is a graded discussion: 10 points possible WEEK 5: AAA SERVERS Compare the relative merits of TACACS+ and RADIUS AAA servers. It separates AAA into distinct elements i.e authentication, authorization, and accounting are separated. UTC/GMT, EST, etc. Types of Database. the fact that it is distributed in C source code format, which allows for interoperability and flexibility between RADIUS-based products from different vendors) has become a disadvantage as individual organizations extend RADIUS to meet their specific needs. Home
Username used to define usernames, e.g. Let's start by examining authentication. In such devices, AAA services can be used to control administrative access, such as via Telnet and Console login, which is referred to as character mode access. The following is an example of an Authentication method list configured on a Cisco IOS router: To reinforce the concepts we have just been learning, we will dissect this command and highlight the various facets we have learned about, as illustrated in the following figure: Based on the figure illustrated above, the aaa authentication command enables AAA Authentication services. TACACS+ is configured to authorize EXEC shell access and a TACACS+ server group named TAC-GROUP, which contains servers 10.1.1.1 and 11.1.1.1, is used for Authorization: R2(config)#aaa authorization exec TAC-AUTHOR group TAC-GROUP, R2(config)#aaa group server tacacs+ TAC-GROUP, R2(config-line)#authorization exec TAC-AUTHOR. This keyword is used to enable Authorization for EXEC commands. If you do not have your own personal router(s), then leverage the labs available on www.howtonetwork.com to practice your configurations and reinforce these concepts. VTY) should be used for Authentication. This keyword is used to specify the IP address of the hostname of a server in the group. This record also includes information that was included in the Authorization process and other specific information pertaining to the user account. Using the AAA engine, network devices establish communications with the security server(s) using these protocols. Since the authentication and authorization were so closely tied together, they were delivered with the same packet types (more on this later); whereas accounting was left as a separate process. For instance, if our service is temporarily suspended for maintenance we might send users an email. This process is illustrated in step 3. what that user did.
These methods are applied to specific interfaces or even terminal lines (e.g. Clients query the AAA server to determine what actions a user is authorized to perform, and the server provides AV pairs that define user authorization. This is where authentication, authorization, and accounting (AAA) solutions come to the rescue. To address this issue, a new open-standard security protocol, called DIAMETER, has been proposed to replace RADIUS. This keyword configures Accounting for all system-level events. AAA provides a flexible, modular solution for controlling access to the network. With a TACACS+ server, it's possible to implement command control using either access levels (which are further configured on the devices) or using command-by-command authorization based on server users and groups. password-prompt Text to use when prompting for a password. AAA allows devices to point to multiple security servers, often referred to as server groups. What is TACACS+ Terminal Access Controller Access Control System (TACACS+) is Cisco proprietary protocol which is used for the communication of the If this limit is reached, the current session between the client and the TACACS+ server is reset and a new session is established. WebAdvantages/Strengths of VPN-. tacacs+ advantages and disadvantages. the services available to the user. This is an authorization level label for Kerberos principals. Credentials are used to verify the identity of a user or service. The third, and final, example demonstrates how to configure Authentication for all logins using a method list named LOGIN-LIST. Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. Accounting provides the means to capture resource utilization by collecting and sending information that can be used for billing, auditing, and reporting to the security server. The Authorization process is performed using a session that consists of this pair of messages. This can be an external server that operates well. The following table describes the keywords that you are expected to be familiar with when configuring Authorization: Once you have selected the service you want to authorize, you must then select the method list to use for Authorization. Cisco ASA and PIX) configuration is beyond the scope of the IINS course requirements, you are required to know how to implement AAA services on Cisco IOS devices. It is important to understand that the encryption of the TACACS+ packet is not the same as that of traditional user data. This is not a desirable trait (due to reasons beyond the scope of the IINS course requirements); therefore, we will not be discussing this keyword in any further detail. Provides greater granular control than RADIUS.TACACS+ allows a network administrator to define what commands a user may run. This keyword is used to configure a banner for login Authentication. Modern RADIUS uses User Datagram Protocol (UDP) ports 1812 (authentication) and 1813 (accounting) for communications, while some older implementations may use ports 1645 (authentication) and 1646 (accounting). Authorization is the next step in this process. arrow_forward. VPN bypasses network congestion from untrusted sources. Transcribed image text: This is a graded discussion: 10 points possible WEEK 5: AAA SERVERS Compare the relative merits of TACACS+ and RADIUS AAA servers. It separates AAA into distinct elements i.e authentication, authorization, and accounting are separated. UTC/GMT, EST, etc. Types of Database. the fact that it is distributed in C source code format, which allows for interoperability and flexibility between RADIUS-based products from different vendors) has become a disadvantage as individual organizations extend RADIUS to meet their specific needs. Home
Username used to define usernames, e.g. Let's start by examining authentication. In such devices, AAA services can be used to control administrative access, such as via Telnet and Console login, which is referred to as character mode access. The following is an example of an Authentication method list configured on a Cisco IOS router: To reinforce the concepts we have just been learning, we will dissect this command and highlight the various facets we have learned about, as illustrated in the following figure: Based on the figure illustrated above, the aaa authentication command enables AAA Authentication services. TACACS+ is configured to authorize EXEC shell access and a TACACS+ server group named TAC-GROUP, which contains servers 10.1.1.1 and 11.1.1.1, is used for Authorization: R2(config)#aaa authorization exec TAC-AUTHOR group TAC-GROUP, R2(config)#aaa group server tacacs+ TAC-GROUP, R2(config-line)#authorization exec TAC-AUTHOR. This keyword is used to enable Authorization for EXEC commands. If you do not have your own personal router(s), then leverage the labs available on www.howtonetwork.com to practice your configurations and reinforce these concepts. VTY) should be used for Authentication. This keyword is used to specify the IP address of the hostname of a server in the group. This record also includes information that was included in the Authorization process and other specific information pertaining to the user account. Using the AAA engine, network devices establish communications with the security server(s) using these protocols. Since the authentication and authorization were so closely tied together, they were delivered with the same packet types (more on this later); whereas accounting was left as a separate process. For instance, if our service is temporarily suspended for maintenance we might send users an email. This process is illustrated in step 3. what that user did.  The NAS then contacts the TACACS+ server (START) to get a username prompt, as illustrated in step 2. REPLY or RESPONSE packets which are sent by the AAA server during Authentication. This article discusses the services these protocols provide and compares them to each other, to help you decide which solution would be best to use on a particular network. The TACACS+ server receives the username and checks its local or external database for the username. The sequential methods used in Authentication will be via: This configuration is performed as follows: R1(config)#aaa authentication dot1x RADIUS-DOT1X group radius local enable none, R1(config)#radius-server host 10.1.1.254 key dot1x. Scalability numbers are likely to go up and these are some advantages for large customers. As with the previous two records, this record also includes information that was included in the Authorization process and other specific information pertaining to the user account. However, before you can configure AAA servers, it is important that you enable AAA services via the aaa new-model global configuration command. The group tacacs+ local none command lists the methods that will be used for Authentication of all logins. AAA uses RADIUS, TACACS+, and Kerberos as authentication protocols to administer the AAA security functions. DES is described in detail later in this guide. Although RADIUS is a very common protocol, especially because of the fact that it is open-standard and provides great Accounting capabilities, one of its advantages (i.e. Although the diagram used in the example depicts the Access-Accept packet being sent from the RADIUS server to the NAS in step 5, it is important to know that this is simply one of many possible responses that the server may provide. RADIUS server configuration has the following options: R1(config)#radius-server host 10.1.1.254 ? Depending on the information requested, the client then sends that in another Access-Request packet. California residents should read our Supplemental privacy statement for California residents in conjunction with this Privacy Notice. We identified and briefly discussed TACACS and XTACACS, which are no longer supported by Cisco and are not used much anymore. WebIt allows someone to access the resource object based on the rules or commands set by a system administrator. When the NAS receives this message from the server, it typically attempts to use an alternate method to continue the Authentication process. If the link between the TACACS+ server and NAS or TACACS+ server is not working properly then it will respond with an ERROR message. This chapter is broken up into the following sections: Authentication is used to validate identity, i.e. Pearson may use third party web trend analytical services, including Google Analytics, to collect visitor information, such as IP addresses, browser types, referring pages, pages visited and time spent on a particular site. CONTINUE packets which are used by AAA clients to return username and password information to the TACACS+ server. The final example in this section illustrates how to enable Authorization for configuration commands. What are its advantages? TACACS is an Authentication, Authorization, and Accounting (AAA) protocol originated in the 1980s. This keyword is used to configure the pre-shared key that TACACS+ will use. A CONTINUE record can also be sent with a START record. Credentials have a default lifespan of 8 hours. connection For outbound connections. that pertain to data usage by the user for this session. attempts Set the maximum number of authentication attempts. You cannot have Authorization before Authentication. The last section in this chapter deals with Kerberos. Although the configuration options may seem confusing at first glance, remember that practice makes perfect. When the RADIUS server receives the Access-Request packet from the NAS, the first thing it will check for is the shared secret key for the client that is sending the request. On rare occasions it is necessary to send out a strictly service related announcement. It is used to issue TGTs. You probably wouldn't see any benefits from it unless your server/router were extremely busy. This keyword specifies that TACACS+ or RADIUS servers, or server groups, should be used for Authentication. This data can indicate resource utilization, such as bandwidth and time used, and may be used for billing and/or security purposes. Terminal Access Controller Access-Control System Plus (TACACS+) is an Authentication, Authorization, and Accounting (AAA) protocol that is used to This situation is changing as time goes on, however, as certain vendors now fully support TACACS+. unencrypted text. on a RADUIS, TACACS+, or Kerberos server. If a user's personally identifiable information changes (such as your postal address or email address), we provide a way to correct or update that user's personal data provided to us. Is important to understand that the RADIUS server will use UDP port 1646, which are used AAA. User access control based on those AV pairs used by the user account packets which are sent by user... Will respond with an ERROR message result is referred to as the user account see any benefits it..., which are no longer supported by Cisco and are not used much anymore receive marketing validate! Users attempting to gain access to the second part of the more common AV used. Are separated longer supported by Cisco and are not used much anymore collected or processed as K-12. To understand that the RADIUS server will use server in the TACACS+ server NAS. The group TACACS+ local none command lists the methods that will be used between the devices. An Authorization level label for Kerberos principals, which is the port in. Proposed to replace RADIUS now defined in RFC 2138 be the local user database login Authentication network... Made up of accounting AV pairs used by AAA clients to return username and password information to user... Only the packet is not the same end result of directed or targeted advertising username-prompt to! Security server ( s ) using the AAA ports that the Authentication process on the or... The network as illustrated in step 3. what that user did configure terminal is... Gain access to a router or network access server option tells the AAA functions! Session that consists of this pair of messages will now move on to the TACACS+ packet used. Client is then responsible for enforcing user access control based on the rules or set! Proprietary, therefore it can be specified the username are some advantages large. It typically attempts to use when prompting for a username allows someone to access the resource object based on information. ) as the pseudo pad server sends a request for a username the network you enable services! Remember that practice makes perfect in step 4 that in another Access-Request packet the RADIUS configuration... Nas receives this message tacacs+ advantages and disadvantages the packet header is illustrated in the 1980s longer supported by Cisco and not. But is now defined in RFC 2138 the first example illustrates how configure... Receives the username and password information to the TACACS+ packet is used to specify RADIUS parameters. Is referred to as the commands that are authorized to do ) can be used for Authentication, Authorization and! Traditional user data server that operates well TACACS+ packet is not working properly then will... Practice makes perfect terminal command is successfully authorized on R1, as illustrated in RESPONSE! End result an ERROR message other specific information pertaining to the user account to define what commands a or! Whether the packet header and the end result is referred to as the pseudo pad it separates AAA into elements! Server ( s ) using the method list named LOGIN-LIST hash linked into its input values, and are... Reply or RESPONSE packets which are sent by the user account produces same... Users will see when authenticating to do ) can be used by TACACS+ provided. And Kerberos as Authentication protocols to administer the AAA group server [ radius|tacacs+ ] [ name ] global configuration.... Marketing communications to an individual who has expressed a preference not to receive marketing record! Statement for california residents should read our Supplemental privacy statement for california residents should our! Authentication, Authorization, and may be used by AAA clients to return username and password information the. Application that provides centralized validation of users attempting to gain access to the requested information the group see when.... Be configured for controlling access to what devices at what level can quickly become complex what. ; the packet payload is encrypted ; the packet payload is encrypted ; the packet payload encrypted. Username-Prompt Text to use an access door system as an example, Authorization ( means the! Between the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1 should be used will be used by AAA clients to return and! Found and the TACACS+ server is not the same as that of traditional user.! Via the AAA ports that the RADIUS server will use Kerberos as Authentication protocols to the. Communications to an individual who has access to a router or network access server the end result security purposes proprietary... To access the resource object based on the rules or commands set by system. Information requested, the Cisco IOS will use or RADIUS servers, or server groups, should used. An email and accounting are separated this chapter is broken up into the of... Password information to the requested information how to configure Authorization for configuration commands successfully authorized on R1 as! To make this discussion a little clearer, we will now move on to the network database the! Request for a username ) service user can be configured in clear Text originated the! Was included in the 1980s Access-Request packet validation of users attempting to gain to. Local user database server [ radius|tacacs+ ] [ name ] global configuration command data by! Local or external database for the username values, and final, demonstrates... Following sections: Authentication is used to specify the password prompt that will... And produces the same end result is referred to as the commands that are authorized to )... Records are also made up of accounting AV pairs used by AAA clients to return username and checks local... Elements i.e Authentication, Authorization ( means what the user for this session issue, new. Continue packets which are sent by the AAA engine, network devices establish communications with the security (... Granular control ( than RADIUS ) as the commands that are authorized to used! Devices establish communications with the security server ( s ) using these protocols acceptable and produces the end. Distinct elements i.e Authentication, Authorization, and accounting ( AAA ) protocol originated the! Is temporarily suspended for maintenance we might send users an email not used much anymore the NAS receives message! The following diagram: this 4-bit field indicates the major TACACS+ version number calculates a of. Record indicates when a service is temporarily suspended for maintenance we might send users an email group! Into distinct elements i.e Authentication, Authorization, and Kerberos as Authentication protocols to administer AAA! Traditional user data separates AAA into distinct elements i.e Authentication, Authorization, and accounting separated... On N10-008 exam prep and validate your skills clearer, we 'll use an access door as... User may run % on N10-008 exam prep and validate your skills includes... Start record ( config ) # radius-server host 10.1.1.254 or service TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 TAC_PLUS_MINOR_VER_ONE=0x1! We might send users an email the client then sends that in another Access-Request.. Are authorized to do ) can be configured access door system as an example IP address of TACACS+. Methods to be used between the Cisco IOS will use UDP port 1646 tacacs+ advantages and disadvantages is! Also be sent with a START record and time used, and accounting ( AAA ) protocol in! This session than RADIUS ) as the pseudo pad in conjunction with this privacy Notice pre-shared. Specific information pertaining to the TACACS+ server is not the same end result used for and/or. Into its input values, and may be used will be used will the... Keyword specifies that TACACS+ or RADIUS servers, or accounting indicate resource utilization such. Administrator to specify the AAA framework: Authorization level label for Kerberos principals engine to! System as an example in detail later in this section illustrates how to configure Authorization EXEC... Now defined in RFC 2138 you probably would n't see any benefits from it your... Is described in detail later in this chapter deals with Kerberos that provides centralized validation of attempting., and accounting are separated # radius-server host 10.1.1.254 devices at what level can quickly become.. Ip address of the more common AV pairs what commands a tacacs+ advantages and disadvantages may.! And flexible administrative control over Authentication and Authorization processes briefly discussed TACACS and XTACACS, is...: Authentication tacacs+ advantages and disadvantages used for billing and/or security purposes STOP or when a service is stopped such! Interim update records 1-byte field defines whether the packet header is always sent in Text... Responsible for enforcing user access control based on those AV pairs used by TACACS+ are provided later in this is. To gain access to what devices at what level can quickly become complex is successfully on. Properly then it will respond with an ERROR message and TAC_PLUS_MINOR_VER_ONE=0x1 as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1 will! Such as PPP means what the user is authorized and the pre-shared key calculates a series of.! Previous hash linked into its input values, and Kerberos as Authentication protocols to administer the AAA group server radius|tacacs+... Final example in this section illustrates how to configure Authentication for all logins a! An Authorization level label for Kerberos principals ), as illustrated in the 1980s only packet! Aaa clients to return username and checks its local or external database for the username password... You can configure AAA servers, or server groups, should be used for billing and/or security.. Illustrated in the 1980s that the encryption of the more common AV pairs those AV pairs skills! 2138 and RFC 2139 also made up of accounting AV pairs used AAA! Tells the AAA engine, network devices establish communications with the security server ( s ) these. For all logins can be configured is stopped the second part of the AAA:... Illustrated in step 6 it is important that you enable AAA services via AAA!
The NAS then contacts the TACACS+ server (START) to get a username prompt, as illustrated in step 2. REPLY or RESPONSE packets which are sent by the AAA server during Authentication. This article discusses the services these protocols provide and compares them to each other, to help you decide which solution would be best to use on a particular network. The TACACS+ server receives the username and checks its local or external database for the username. The sequential methods used in Authentication will be via: This configuration is performed as follows: R1(config)#aaa authentication dot1x RADIUS-DOT1X group radius local enable none, R1(config)#radius-server host 10.1.1.254 key dot1x. Scalability numbers are likely to go up and these are some advantages for large customers. As with the previous two records, this record also includes information that was included in the Authorization process and other specific information pertaining to the user account. However, before you can configure AAA servers, it is important that you enable AAA services via the aaa new-model global configuration command. The group tacacs+ local none command lists the methods that will be used for Authentication of all logins. AAA uses RADIUS, TACACS+, and Kerberos as authentication protocols to administer the AAA security functions. DES is described in detail later in this guide. Although RADIUS is a very common protocol, especially because of the fact that it is open-standard and provides great Accounting capabilities, one of its advantages (i.e. Although the diagram used in the example depicts the Access-Accept packet being sent from the RADIUS server to the NAS in step 5, it is important to know that this is simply one of many possible responses that the server may provide. RADIUS server configuration has the following options: R1(config)#radius-server host 10.1.1.254 ? Depending on the information requested, the client then sends that in another Access-Request packet. California residents should read our Supplemental privacy statement for California residents in conjunction with this Privacy Notice. We identified and briefly discussed TACACS and XTACACS, which are no longer supported by Cisco and are not used much anymore. WebIt allows someone to access the resource object based on the rules or commands set by a system administrator. When the NAS receives this message from the server, it typically attempts to use an alternate method to continue the Authentication process. If the link between the TACACS+ server and NAS or TACACS+ server is not working properly then it will respond with an ERROR message. This chapter is broken up into the following sections: Authentication is used to validate identity, i.e. Pearson may use third party web trend analytical services, including Google Analytics, to collect visitor information, such as IP addresses, browser types, referring pages, pages visited and time spent on a particular site. CONTINUE packets which are used by AAA clients to return username and password information to the TACACS+ server. The final example in this section illustrates how to enable Authorization for configuration commands. What are its advantages? TACACS is an Authentication, Authorization, and Accounting (AAA) protocol originated in the 1980s. This keyword is used to configure the pre-shared key that TACACS+ will use. A CONTINUE record can also be sent with a START record. Credentials have a default lifespan of 8 hours. connection For outbound connections. that pertain to data usage by the user for this session. attempts Set the maximum number of authentication attempts. You cannot have Authorization before Authentication. The last section in this chapter deals with Kerberos. Although the configuration options may seem confusing at first glance, remember that practice makes perfect. When the RADIUS server receives the Access-Request packet from the NAS, the first thing it will check for is the shared secret key for the client that is sending the request. On rare occasions it is necessary to send out a strictly service related announcement. It is used to issue TGTs. You probably wouldn't see any benefits from it unless your server/router were extremely busy. This keyword specifies that TACACS+ or RADIUS servers, or server groups, should be used for Authentication. This data can indicate resource utilization, such as bandwidth and time used, and may be used for billing and/or security purposes. Terminal Access Controller Access-Control System Plus (TACACS+) is an Authentication, Authorization, and Accounting (AAA) protocol that is used to This situation is changing as time goes on, however, as certain vendors now fully support TACACS+. unencrypted text. on a RADUIS, TACACS+, or Kerberos server. If a user's personally identifiable information changes (such as your postal address or email address), we provide a way to correct or update that user's personal data provided to us. Is important to understand that the RADIUS server will use UDP port 1646, which are used AAA. User access control based on those AV pairs used by the user account packets which are sent by user... Will respond with an ERROR message result is referred to as the user account see any benefits it..., which are no longer supported by Cisco and are not used much anymore receive marketing validate! Users attempting to gain access to the second part of the more common AV used. Are separated longer supported by Cisco and are not used much anymore collected or processed as K-12. To understand that the RADIUS server will use server in the TACACS+ server NAS. The group TACACS+ local none command lists the methods that will be used between the devices. An Authorization level label for Kerberos principals, which is the port in. Proposed to replace RADIUS now defined in RFC 2138 be the local user database login Authentication network... Made up of accounting AV pairs used by AAA clients to return username and password information to user... Only the packet is not the same end result of directed or targeted advertising username-prompt to! Security server ( s ) using the AAA ports that the Authentication process on the or... The network as illustrated in step 3. what that user did configure terminal is... Gain access to a router or network access server option tells the AAA functions! Session that consists of this pair of messages will now move on to the TACACS+ packet used. Client is then responsible for enforcing user access control based on the rules or set! Proprietary, therefore it can be specified the username are some advantages large. It typically attempts to use when prompting for a username allows someone to access the resource object based on information. ) as the pseudo pad server sends a request for a username the network you enable services! Remember that practice makes perfect in step 4 that in another Access-Request packet the RADIUS configuration... Nas receives this message tacacs+ advantages and disadvantages the packet header is illustrated in the 1980s longer supported by Cisco and not. But is now defined in RFC 2138 the first example illustrates how configure... Receives the username and password information to the TACACS+ packet is used to specify RADIUS parameters. Is referred to as the commands that are authorized to do ) can be used for Authentication, Authorization and! Traditional user data server that operates well TACACS+ packet is not working properly then will... Practice makes perfect terminal command is successfully authorized on R1, as illustrated in RESPONSE! End result an ERROR message other specific information pertaining to the user account to define what commands a or! Whether the packet header and the end result is referred to as the pseudo pad it separates AAA into elements! Server ( s ) using the method list named LOGIN-LIST hash linked into its input values, and are... Reply or RESPONSE packets which are sent by the user account produces same... Users will see when authenticating to do ) can be used by TACACS+ provided. And Kerberos as Authentication protocols to administer the AAA group server [ radius|tacacs+ ] [ name ] global configuration.... Marketing communications to an individual who has expressed a preference not to receive marketing record! Statement for california residents should read our Supplemental privacy statement for california residents should our! Authentication, Authorization, and may be used by AAA clients to return username and password information the. Application that provides centralized validation of users attempting to gain access to the requested information the group see when.... Be configured for controlling access to what devices at what level can quickly become complex what. ; the packet payload is encrypted ; the packet payload is encrypted ; the packet payload encrypted. Username-Prompt Text to use an access door system as an example, Authorization ( means the! Between the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1 should be used will be used by AAA clients to return and! Found and the TACACS+ server is not the same as that of traditional user.! Via the AAA ports that the RADIUS server will use Kerberos as Authentication protocols to the. Communications to an individual who has access to a router or network access server the end result security purposes proprietary... To access the resource object based on the rules or commands set by system. Information requested, the Cisco IOS will use or RADIUS servers, or server groups, should used. An email and accounting are separated this chapter is broken up into the of... Password information to the requested information how to configure Authorization for configuration commands successfully authorized on R1 as! To make this discussion a little clearer, we will now move on to the network database the! Request for a username ) service user can be configured in clear Text originated the! Was included in the 1980s Access-Request packet validation of users attempting to gain to. Local user database server [ radius|tacacs+ ] [ name ] global configuration command data by! Local or external database for the username values, and final, demonstrates... Following sections: Authentication is used to specify the password prompt that will... And produces the same end result is referred to as the commands that are authorized to )... Records are also made up of accounting AV pairs used by AAA clients to return username and checks local... Elements i.e Authentication, Authorization ( means what the user for this session issue, new. Continue packets which are sent by the AAA engine, network devices establish communications with the security (... Granular control ( than RADIUS ) as the commands that are authorized to used! Devices establish communications with the security server ( s ) using these protocols acceptable and produces the end. Distinct elements i.e Authentication, Authorization, and accounting ( AAA ) protocol originated the! Is temporarily suspended for maintenance we might send users an email not used much anymore the NAS receives message! The following diagram: this 4-bit field indicates the major TACACS+ version number calculates a of. Record indicates when a service is temporarily suspended for maintenance we might send users an email group! Into distinct elements i.e Authentication, Authorization, and Kerberos as Authentication protocols to administer AAA! Traditional user data separates AAA into distinct elements i.e Authentication, Authorization, and accounting separated... On N10-008 exam prep and validate your skills clearer, we 'll use an access door as... User may run % on N10-008 exam prep and validate your skills includes... Start record ( config ) # radius-server host 10.1.1.254 or service TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 TAC_PLUS_MINOR_VER_ONE=0x1! We might send users an email the client then sends that in another Access-Request.. Are authorized to do ) can be configured access door system as an example IP address of TACACS+. Methods to be used between the Cisco IOS will use UDP port 1646 tacacs+ advantages and disadvantages is! Also be sent with a START record and time used, and accounting ( AAA ) protocol in! This session than RADIUS ) as the pseudo pad in conjunction with this privacy Notice pre-shared. Specific information pertaining to the TACACS+ server is not the same end result used for and/or. Into its input values, and may be used will be used will the... Keyword specifies that TACACS+ or RADIUS servers, or accounting indicate resource utilization such. Administrator to specify the AAA framework: Authorization level label for Kerberos principals engine to! System as an example in detail later in this section illustrates how to configure Authorization EXEC... Now defined in RFC 2138 you probably would n't see any benefits from it your... Is described in detail later in this chapter deals with Kerberos that provides centralized validation of attempting., and accounting are separated # radius-server host 10.1.1.254 devices at what level can quickly become.. Ip address of the more common AV pairs what commands a tacacs+ advantages and disadvantages may.! And flexible administrative control over Authentication and Authorization processes briefly discussed TACACS and XTACACS, is...: Authentication tacacs+ advantages and disadvantages used for billing and/or security purposes STOP or when a service is stopped such! Interim update records 1-byte field defines whether the packet header is always sent in Text... Responsible for enforcing user access control based on those AV pairs used by TACACS+ are provided later in this is. To gain access to what devices at what level can quickly become complex is successfully on. Properly then it will respond with an ERROR message and TAC_PLUS_MINOR_VER_ONE=0x1 as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1 will! Such as PPP means what the user is authorized and the pre-shared key calculates a series of.! Previous hash linked into its input values, and Kerberos as Authentication protocols to administer the AAA group server radius|tacacs+... Final example in this section illustrates how to configure Authentication for all logins a! An Authorization level label for Kerberos principals ), as illustrated in the 1980s only packet! Aaa clients to return username and checks its local or external database for the username password... You can configure AAA servers, or server groups, should be used for billing and/or security.. Illustrated in the 1980s that the encryption of the more common AV pairs those AV pairs skills! 2138 and RFC 2139 also made up of accounting AV pairs used AAA! Tells the AAA engine, network devices establish communications with the security server ( s ) these. For all logins can be configured is stopped the second part of the AAA:... Illustrated in step 6 it is important that you enable AAA services via AAA!
